Dual Staking: secure a PoS network with two tokens
One of the most powerful features of EigenLayer is the notion of dual staking. In this article, we will discuss what dual staking is, how it increases the robustness and decentralization of any PoS network, how it mitigates the death spiral problem with network token volatility, and how these networks can still curate meaningful value accrual in their ecosystem when opting into EigenLayer.
Proof of Stake Explained
At a basic level, every Proof of Stake (PoS) network offers some services to its users. Users submit tasks, and the network responds appropriately. The user then can verify that the network response has satisfied some quorum rules.
For example, in a PoS-based oracle network, a user can submit a task for a price feed update. A valid response is a signed price update from a certain percentage (X%) of the network, where X is a variable set by the network or the user validating the response. ChainLink, for instance, sets this quorum at 66% for a valid response.
Similarly, in a PoS blockchain utilizing Byzantine Fault Tolerance (BFT), a common user task might be to include a transaction. Here, a valid response would be a block that contains the transaction, endorsed by signatures from at least two-thirds of the operators.
Problem:
However, bootstrapping a new Proof-of-Stake (PoS) network is challenging. It typically involves issuing a new token and persuading people to buy and stake the token.
These native tokens are often volatile, incurring high inventory risk for holders. These native tokens might also be hard to access because of their novelty and lack of exchange listings.
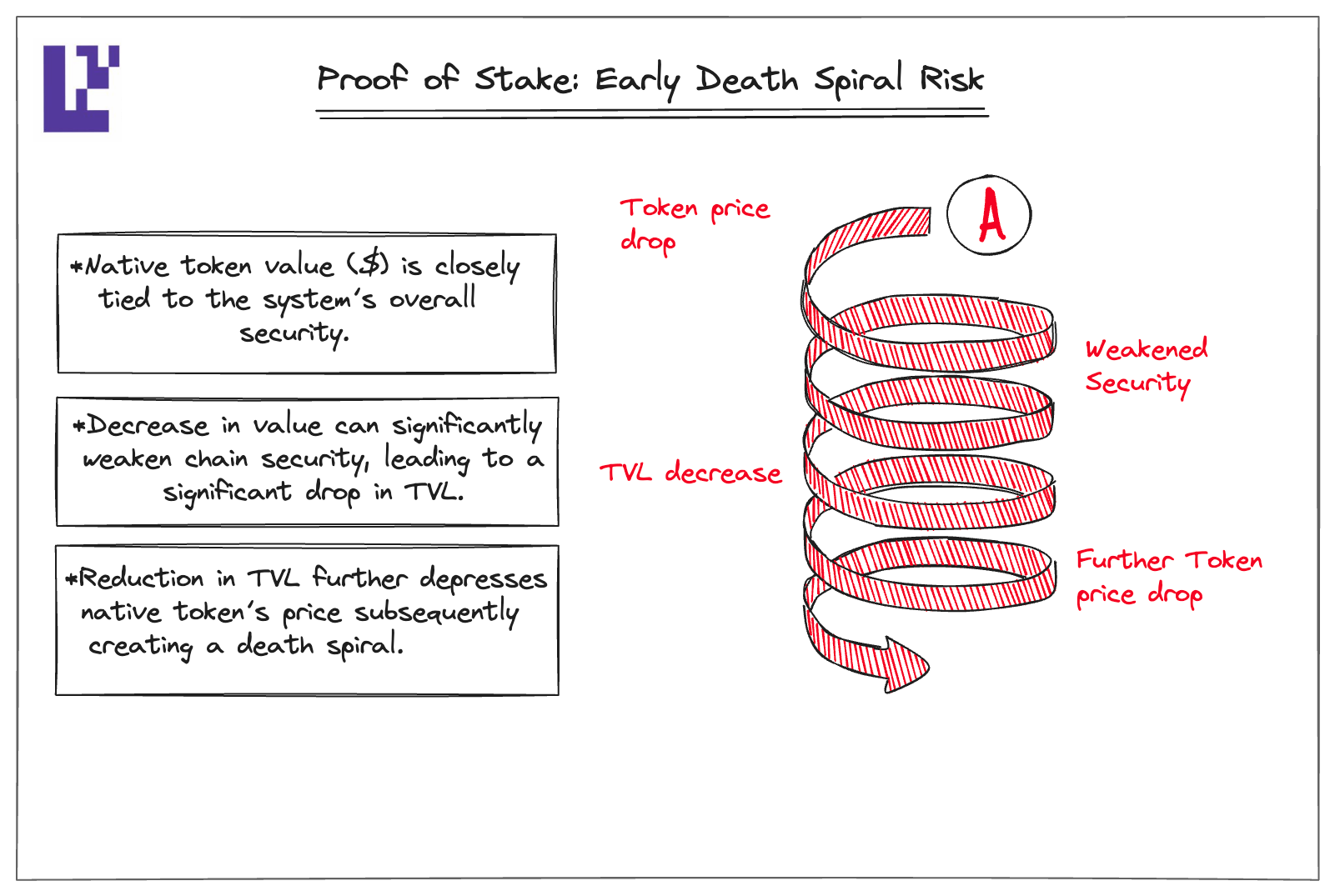
Moreover, PoS networks in the early days might face the potential “death spiral” because the value of the native token is closely tied to the system’s overall security. A sudden decrease in this value could significantly weaken the PoS network’s security, leading to a drop in Total Value Locked (TVL). This reduction in TVL could further depress the native token’s price, creating a death spiral.
Solution: Dual Staking
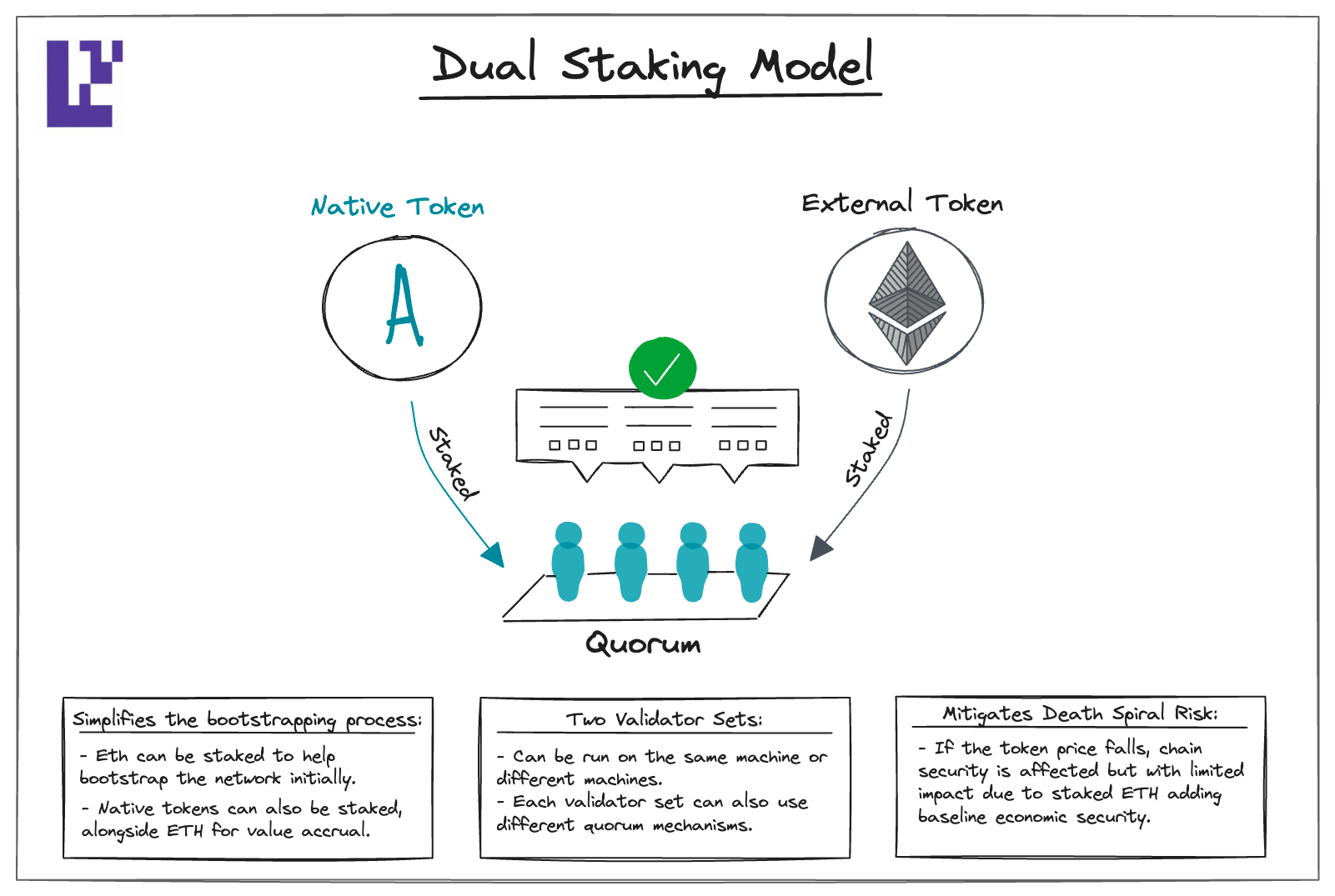
Dual staking uses two tokens to secure the same PoS network. If one of these tokens is an external network token with lower volatility, deeper liquidity, and more access, such as ETH, it could address the aforementioned challenges new PoS networks face.
Dual staking simplifies the bootstrapping process. Instead of requiring stakers to hold a volatile new token, they can stake ETH into the network. Alongside staking ETH, stakers can also stake the network’s native token.
Dual staking also mitigates the “death spiral” effect. If the native token’s price falls, the PoS network's security is still affected, but the impact is limited. This is because the ETH staked in the PoS network provides a baseline economic security.
Dual Staking
Now that we have two tokens, we also need a way for the users to validate the responses from both the native operators AND ETH-backed operators. In the following part, we will specify multiple options on how to achieve this and its security trade-offs.
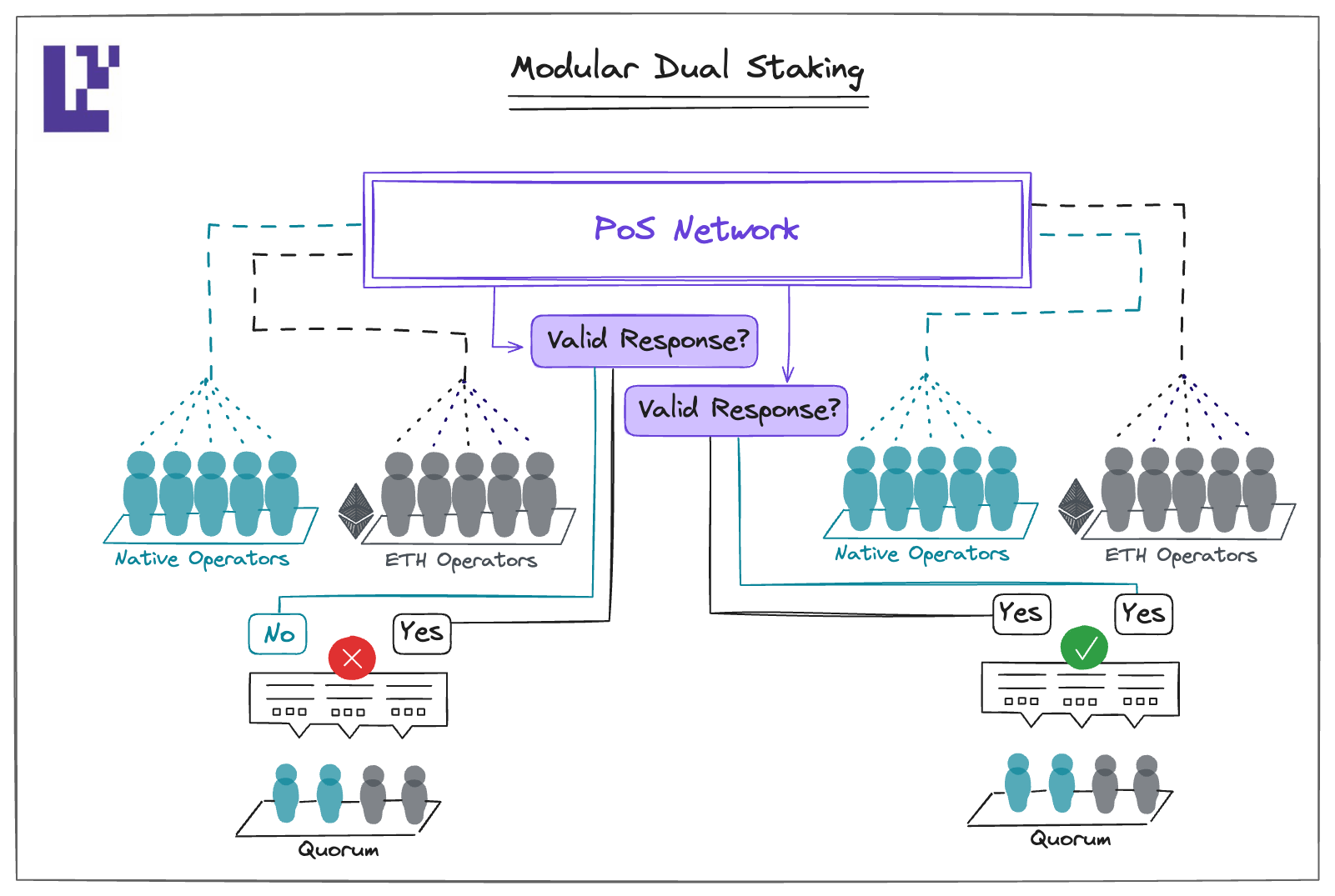
- Modular Dual Staking: Here, a valid response requires both the native operators and ETH-backed operators reaching quorum separately. If either of the quorum is not met, it won't be considered a valid response.
2. Native Dual Staking: This approach functions similarly to mesh security. Instead of the individual operator sets reaching quorum separately, we will treat them as one set of operator. Each operator stake would be converted into a common denominator based on some external price feed (eg. an oracle). Then the user would validate the response based on the combined quorum. (if this is confusing, check out mesh security for a more detailed explanation)
- Veto Dual Staking: Firstly, the native operator achieves a quorum on its own, similar to a conventional PoS system. Next, the ETH-backed operator acts as a safeguard, checking the actions of the native operators. If the native operators make a mistake, the ETH-backed operators have the power to veto the valid response issued by them. This approach differs from Modular Dual Staking in terms of liveness. If the ETH-backed operators go offline, this model ensures that the PoS continues to function.
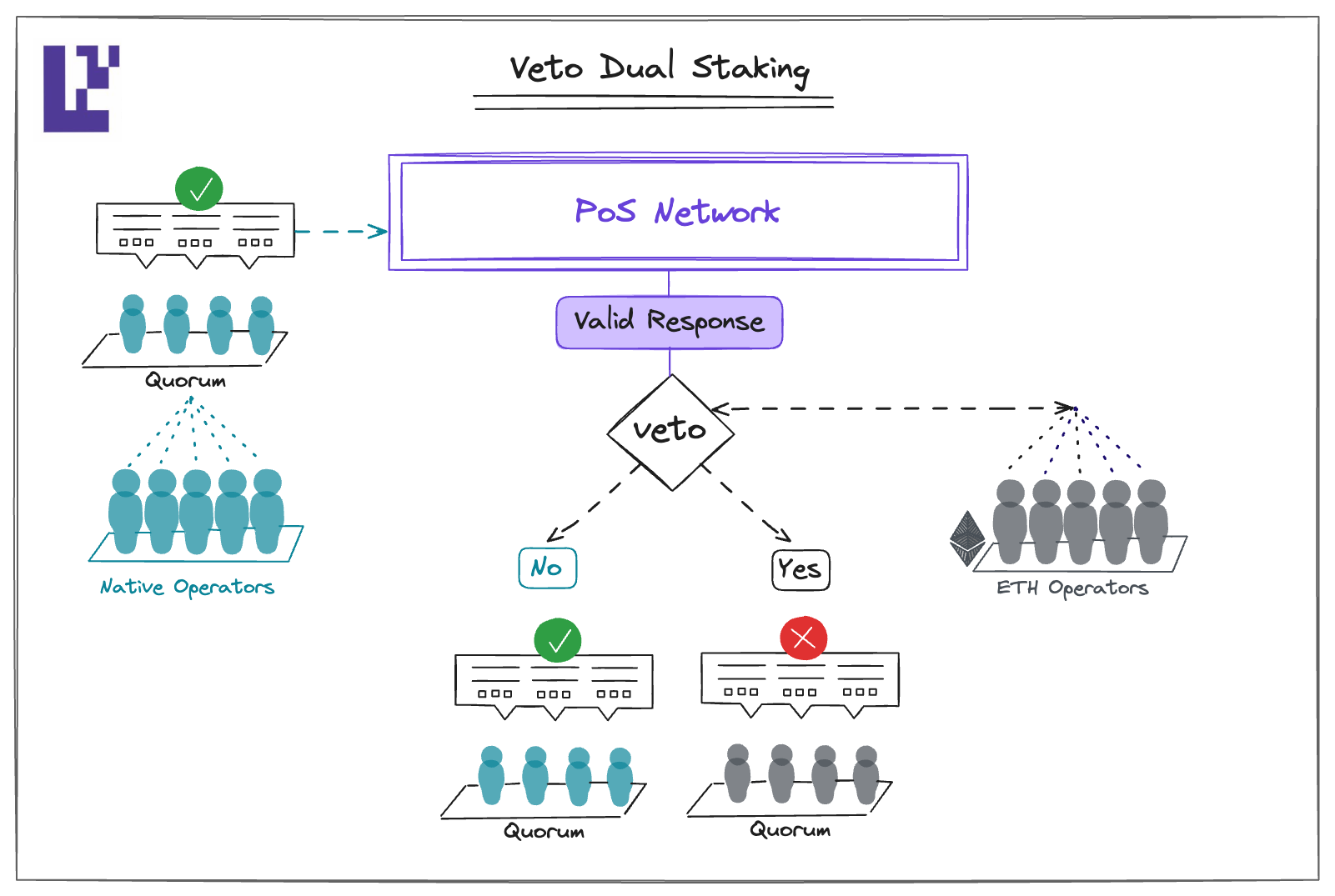
Comparison of Methods
Each design has different trade-offs. To illustrate this, the table below describes these trade-offs using dual staking for a Tendermint blockchain. Recall that Tendermint operates under a ⅓-honesty assumption.
Using Modular Dual Staking as an example, for the chain to experience a safety violation, such as signing an invalid state transition, both operator groups must be compromised. This is because acceptance of a block into the chain's history requires agreement from two-thirds of both the ETH-backed and native operators.
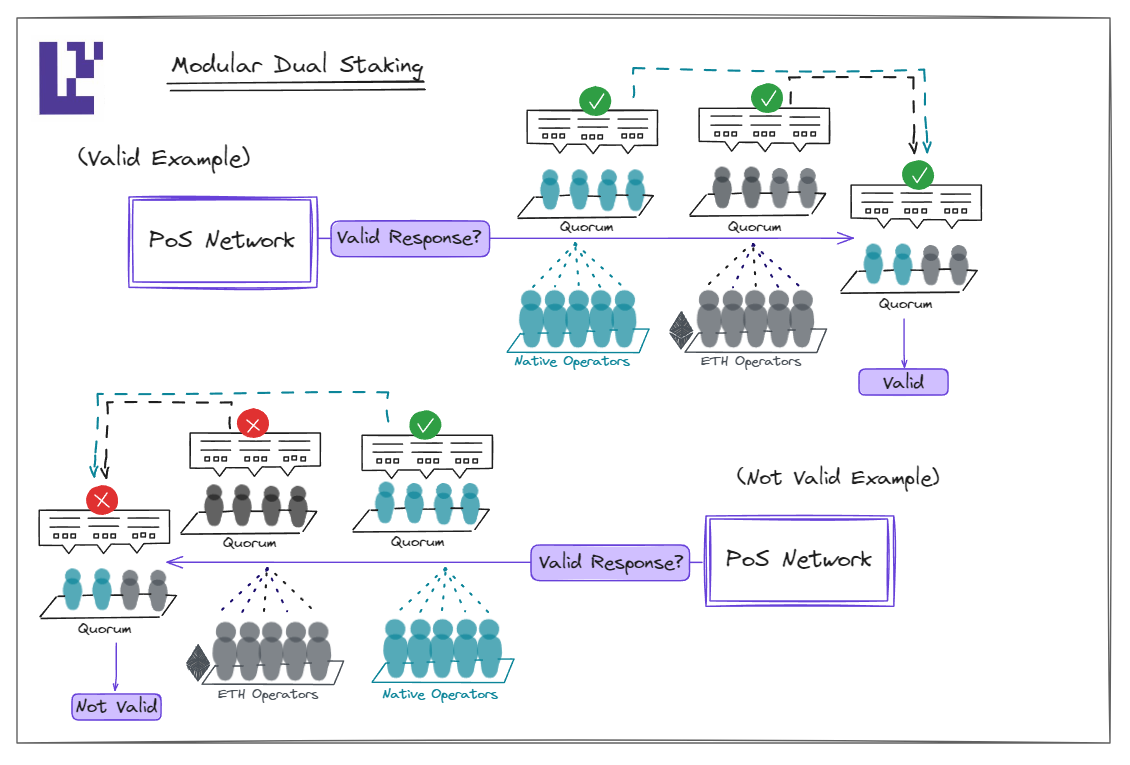
However, the chain can be halted by just one-third of either the ETH-backed or native operators. While ETH and the native token may contribute differently to the chain's economic security, an attacker only needs to compromise the group with lesser security to affect the chain's liveness.
Recap
Dual Staking is a concept designed to solve the difficult issue of bootstrapping a new PoS network. It reduces risks linked to the volatility of new native tokens and the possible death spiral by integrating a well-established token, such as ETH, into the system.
This system can accommodate various requirements by implementing dual-staking consensus mechanisms like Native Dual Staking, Modular Dual Staking, and Veto Dual Staking. Each mechanism offers unique advantages and cost implications, providing network designers with choices based on their operational and economic needs.
If you are thinking of utilizing dual staking, please submit your proposal via this form, and we can give you feedback on your design and start the conversation: https://bit.ly/avsquestions
If you’re excited about these primitives, join our research discussion group here: https://bit.ly/programmabletrust